Top Guidelines Of Security System Installer
Table of ContentsExamine This Report about Security System InstallerAbout Security System Installer5 Simple Techniques For Security System InstallerSecurity System Installer for BeginnersThe Only Guide to Security System InstallerIndicators on Security System Installer You Need To Know
Wireless monitoring makes use of radio signals to attach devices in your residence, allowing the sensing units to send signals to the base terminal. This results in a push notification on your phone or a phone call to the surveillance. Get a cordless security system to make installment less complicated, simplify moving to a brand-new residence, and also for performance throughout a power failure.A carbon monoxide sensing unit can conserve lives as well as send out informs when you're house and away. Utilize a flooding sensor to assist avoid severe water damages and to catch concerns with your pipes as well as appliances.
Use a panic necklace to aid individuals that are maturing or have an impairment in an emergency situation.
The 5-Minute Rule for Security System Installer
You have a few choices when it involves making a decision on a security system to. There are pros as well as cons to every sort of system, as well as no single service will function best for all properties (Security System Installer). When making your choice, make sure to weigh the alternatives and select the alarm with advantages that align with your special requirements.

Given that there aren't any wires to run, wireless security system are the easiest to set up. Many cordless systems can be mounted without assistance, although specialist installation is always recommended. Limited array between sensing units Battery adjustments Wireless security system are great for homes as well as small companies. Wired alarm, as the name might suggest, are hard-wired right into your building.
Some Ideas on Security System Installer You Should Know
It's a typical misunderstanding that wired alarm systems do not have the same adaptability or mobile performance as cordless alarm systems. The truth is that several modern wired systems provide the same remote ease of access as wireless systems.
When an alarm system is activated, who gets signaled? With a monitored alarm system, an alert is sent straight to a that can respond promptly to any type of type of danger. If there's a burglary, they'll dispatch the police. If there's a fire, the fire department will certainly be called. Even for incorrect alarm systems, a surveillance service will certainly know just how to handle it.
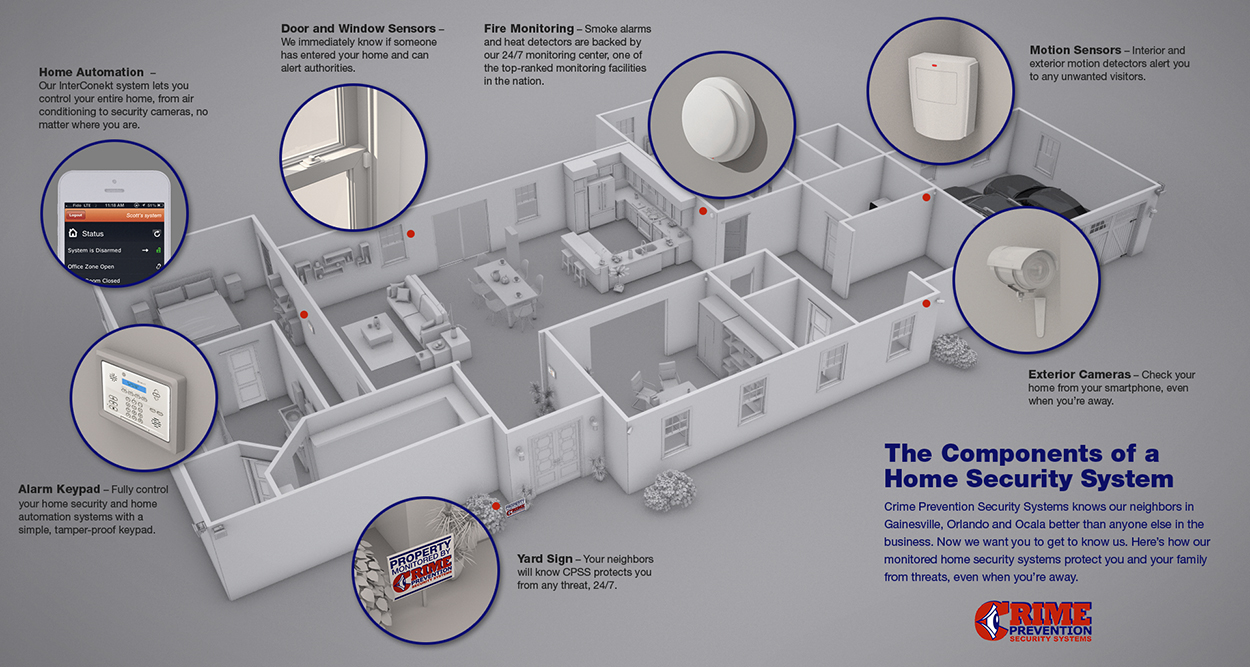
How Security System Installer can Save You Time, Stress, and Money.
If you're interested in specialist monitoring, we can aid with that also! with your concerns or for a cost-free, no obligation quote today.
A monitored alarm system is various contrasted your typical her response safety and security alarm. It has an assigned employees who contacts you when the alarm system goes off to determine if it was a blunder or there is an authentic safety and security breach. If the real safety breach is determined by the personnel, the regional authorities are notified instantly.
It is useful for both business structures and homes. The alarm system contains smoke alarm that are located throughout the home. When these detectors come in contact with heat or smoke, they increase the alarm. You could also choose the one with an indoor lawn sprinkler to enhance your security.
Facts About Security System Installer Revealed
The interesting high quality of CCTV electronic cameras is that you can keep an eye on your house also when you are not about visit the site as they can be accessed remotely. A safety guard is an old-time strategy when it comes to shielding your house.
If you have a big residential or commercial property or reside in a property complex, having a safety guard is an excellent choice. They can straight question an unknown individual attempting to enter your home.
These safety and security systems have hard-wired links to get power and send out signals to a main center. Cables link every sensing unit as well as entry factor in the home. Of course, specialists should install them for you, yet that process could be simpler than anticipated, especially if your home came prewired for such setups.
Some Known Questions About Security System Installer.
They usually have battery backups that maintain running throughout power blackouts. If you lease your residence as well as want a wired safety system, inspect your lease contract or ask your property owner. Equally as an industrial lease clarifies just how much the lessee pays and also what that quantity covers, a residential lease will certainly claim whether you can customize your rental unit during the tenancy.
Tenants and individuals that relocate commonly value the mobility of wireless systems. Their major drawback is that electro-magnetic disturbance from other devices in the vicinity might cause the arrangement to reveal undesirable actions by activating a false alarm system.
Perhaps you want to have a cam in the basement, but only for guidance functions when your youngster and also their pals play down there. Wireless systems streamline those temporary needs. Most modern safety systems come Discover More Here with apps, letting individuals examine statuses, see real-time camera feeds, and also get real-time notices of particular events.